June 17, 2015
OK. That's It. We're Done.


"..."

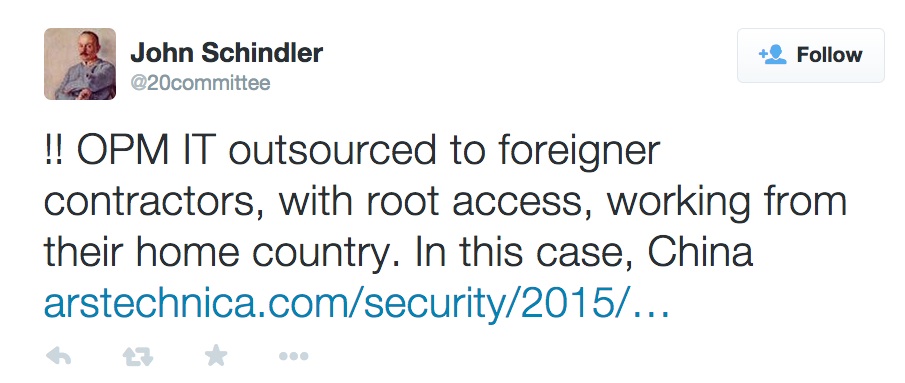
But even if the systems had been encrypted, it likely wouldn't have mattered. Department of Homeland Security Assistant Secretary for Cybersecurity Dr. Andy Ozment testified that encryption would "not have helped in this case" because the attackers had gained valid user credentials to the systems that they attacked...
The Chicoms had ROOT access,. They got everything.
Wait...I've SEEN this movie!

So...the Chinese (and probably the Russians) most likely have a dozen or more Alger Hisses and Julius Rosenbergs working for them now. They may have a chunk of our codes too.
And now, China in the South China Sea and Russia in Eastern Europe, they are making their moves. This is why they are pushing now, because they have the secrets, they have the spies, they know our every vulnerability and this is as good a shot as they will ever have. These developments are not bluffs, they are deadly serious. In no small part because our enemies have, in their eyes, a reasonable expectation now of total victory.
Some questions for our readers in the IT field.
If they had Root access, am I correct in assuming they could have so re-arranged things that the issue with the actual infiltration might still be ongoing?
Obviously the personnel are compromised, that can't be undone, but is it even realistic that this could be fixed? Is real security in a network with the very user friendly access we have come to expect in any way securable?
Only tangentially related, since this does not seem to be a "cloud" issue (hell, it's not really a 'hack' as such), but is "the cloud" in any way realistically securable?
Update: edited last sentence to make sense
Posted by: The Brickmuppet at
06:38 PM
| Comments (6)
| Add Comment
Post contains 292 words, total size 4 kb.
1
Yes, once someone gets root access to your system, you have to burn it down and start again. Everything is suspect.
Network security is a question of layers. You have a firewall that only allows known traffic through. You have authentication that only allows know users through, once they're through the firewall. You have a second factor so that even if a hacker knows the password, they need something else (a hardware token) to actually log in. You have authorisation measures so that a given user only has access to the things they need to do their immediate job. You hash passwords and encrypt data and network traffic, so that if there's a mistake and someone gets hold of it, it's no good to them.
OPM apparently didn't do anything right. Everything they could possibly have screwed up, they did, many times over.
Contrast this with LastPass, which suffered a possible security breach this week. Their passwords are hashed 100,000 times, which means that even if a foreign government got hold of them, they are essentially useless.
Network security is a question of layers. You have a firewall that only allows known traffic through. You have authentication that only allows know users through, once they're through the firewall. You have a second factor so that even if a hacker knows the password, they need something else (a hardware token) to actually log in. You have authorisation measures so that a given user only has access to the things they need to do their immediate job. You hash passwords and encrypt data and network traffic, so that if there's a mistake and someone gets hold of it, it's no good to them.
OPM apparently didn't do anything right. Everything they could possibly have screwed up, they did, many times over.
Contrast this with LastPass, which suffered a possible security breach this week. Their passwords are hashed 100,000 times, which means that even if a foreign government got hold of them, they are essentially useless.
Posted by: Pixy Misa at Thu Jun 18 01:10:36 2015 (2yngH)
2
As for the cloud, security is relative. I would trust Amazon, Google, or Microsoft to at least follow best practices. They each have large full-time staffs of highly competent people doing nothing all day but looking for new security problems and heading them off.
I'm using Amazon and Google cloud services at my day job, and while they're complicated, they are robust and as secure as it's practical to make them.
I'm using Amazon and Google cloud services at my day job, and while they're complicated, they are robust and as secure as it's practical to make them.
Posted by: Pixy Misa at Thu Jun 18 03:06:49 2015 (2yngH)
3
A cloud is simple, really. All it is, you pay someone to borrow his computer. It makes sense economically because you don't have to buy your own computer for every task. Plus, computers are easily shared - more easily than rental cars even. That helps to drive utilization up and costs down in a major way, and that is why everyone loves cloud. With that in mind the security of a cloud hinges on the trust you're putting into the guy who owns the computer you're borrowing (well, renting). If he did not install some bad software on that thing before litting you use it, you're reasonably secure. If he did, you're screwed.
Posted by: Pete Zaitcev at Thu Jun 18 09:05:06 2015 (RqRa5)
4
Yep. Well, plus you're trusting in their competence as well as their honesty; an honest but stupid cloud provider is about as desirable as an honest but stupid nuclear power operator.
Posted by: Pixy Misa at Thu Jun 18 22:23:02 2015 (2yngH)
5
Wasn't Apple's cloud cracked?
Posted by: Steven Den Beste at Fri Jun 19 09:02:23 2015 (+rSRq)
6
Yes, and more than once.
Posted by: Pixy Misa at Sun Jun 21 04:04:02 2015 (PiXy!)
39kb generated in CPU 0.0128, elapsed 0.0863 seconds.
71 queries taking 0.0784 seconds, 385 records returned.
Powered by Minx 1.1.6c-pink.
71 queries taking 0.0784 seconds, 385 records returned.
Powered by Minx 1.1.6c-pink.